Introduction
Passwords are ubiquitous.
We use them to protect everything from our phones to our facebook accounts, from our CRMs to our CMS’s and our computers to our cloud storage.
They are often our only line of defence against unwanted intruders. They are what we use to protect our data, our networks, our systems and our identities.
But we have a problem!
In order for them to work they need to be hard to guess. Well, maybe that’s not so bad. We can all come up with a hard to guess password. But, we are told, we should also have a different password for each account we have. Well, that’s a bit more challenging. Having lots of hard to guess passwords is….hard to manage! We can try and remember them all, and we might manage the ones we use daily, bit the less frequent ones? Not a chance!
And we have a lot of passwords. I’ve just done a quick stock take of the number of passwords I’ve got stored in my password manager. Want to guess how many I’ve got? 658!
I reckon I’ve probably got more than the average person owing to the job I do, but even if the average person as a quarter of those, that’s still a lot of passwords. And no-one is going to remember them all. Even if YOU could, your staff wont!
So what’s our solution?
Well what we usually end up doing is coming up with an easy to remember password that we use for everything. Or perhaps we have a small handful that we share out. Or maybe we use those helpful little prompts in our browser that remember the passwords for us?
None of these solutions are very good or very secure. In this article I’m going to show you why and what you can do about it.
Some statistics
Here are some statistics for you to think about, courtesy of Keeper Security:
- Cybercriminals cost companies over £450 Billion in 2018
- 90% of employee passwords can be cracked in 6 hours or less
- 81% of breaches due to weak passwords security
- 80% re-use passwords
- 60% of SMBs go under within 6 months of a cyberattack
Do these stats worry you? If they don’t then they should!
Here are some more worrying stats. The Top 25 most common passwords used in dictionary-based cyberattacks in 2017 (from Interesting Engineering). More on what dictionary-based cyberattacks are in a mo!
- 123456
- Password
- 12345678
- qwerty
- 12345
- 123456789
- letmein
- 1234567
- football
- iloveyou
- admin
- welcome
- monkey
- login
- abc123
- starwars
- 123123
- dragon
- passw0rd
- master
- hello
- freedom
- whatever
- qazwsx
- trustno1
Even though the list is a few years old, what is amazing is that more recent lists look pretty much the same (try these ones from CSOOnline/SplashData or The National Cyber Security Centre)
Do you recognize any of these? Have you used them? Are you still using them? If you are – change them! You might as well leave your front door wide open at night with a sign saying. “Mr burglar, please come and steal my stuff!”
The bottom line?
Cybersecurity starts with password security
So How do hackers find my password?
Either they need to guess it, you need to tell them it or they steal it
In practice there are five main methods used to do this
- Brute Force: Here a computer is used to randomly generate passwords until it gets the right one. Given the processing power of computers these days, that might not take very long
- Dictionary Attack: This is also where a computer is used, but uses a list or dictionary of commonly used passwords or words. This is much quicker than brute force and can be done in seconds if the password you are trying to find is on the list
- Phishing: The fraudulent practice of sending emails, text messages or phone calls purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords
- Social Engineering: Social engineering is the art of manipulating people so they give up confidential information. Phishing is a type of Social Engineering
- Stolen credentials. This can happen if a company or a website gets hacked and they steal the user database that contains passwords! These are then often made available on the shady part of the internet known as the “dark web”
Obviously passwords could also be found if you write them down and leave them where someone could find them, or if someone is watching as you type them in. This is another way of stealing them so you need to guard against that too! Of course, I’m sure you already are!
So how do we prevent these five methods from affecting us? How do we stop them?
Well, let’s remind ourselves of our password requirements. As we have already said, they should be long and complex.
And the reason why passwords should be long and complex is to make a brute force or dictionary attack impossible. Here’s how it works
Password Length and Complexity
Here’s an example password:
Er3K!fXX$
Most websites will say that’s a strong password and will allow that. But is it a good password? No
It would take about 18 hours to crack that password. An eight digit password has 722 trillion possibilities 722,204,136,308,736 assuming 26 upper and lowercase characters, 10 digits and 10 special characters, but that is nothing to today’s computers.
What if we add four more digits in – Er3K!fXX$nB45
A twelve digit password has 19sextillion (19,408,409,961,765,342,806,016). All of a sudden, that has become a LOT more secure. Length matters
To stop a dictionary attack, obviously we need to avoid obvious words and phrases. That’s why random combinations of letters and symbols and numbers are more secure. However, remembering random words and phrases is impossible so how do we get around it?
The answer is to use a password manager. This is the FIRST thing you need to do. There are many options out there and they can generate and securely store passwords for you so you don’t have to remember your password at all, The password manager will handle it all for you.
Now you might say, what’s wrong with using my web browser to remember passwords? Well, they are not securely stored on your device. Anyone with access to your device could find them quite easily. And if you use a different browser on another device, it won’t know what those passwords are so you will be stuck. Much better to use a password manager that will work across all browsers, all devices and encrypt and store your passwords securely
LastPass is a great option for individuals as it is free, but there are better options if you are managing a business or a small team. We are currently recommending Keeper for businesses as this offers some great features to avoid your staff setting weak passwords or forgetting their logins and it will also cope with some of the more complex websites that require more than just a username and password to login!
How can I stop Phishing?
We have all seen what a phishing attempt looks like and we are starting to get wise and be on the lookout. Obviously the purpose of these is to redirect you to a website that looks like one you are normally use and to enter your login details, including password, for that site. Of course, the site is a fake and its purpose is to gather your login information so that the hacker can then access the real site using your credentials.
Not what you want!
Many people will tell you the only solution for this is education and vigilance and whilst that is important and can help, it is a weak overall strategy.
When I worked for a large University not a month would go by without the IT department having to send out another email warning users not click on links in suspicious looking emails as some users had already done so and compromised their accounts.
Phishing attempts are getting cleverer and even the best of us can be caught off guard.
There are three practical and positive things you can do to either reduce phishing, or reduce the chances of a data breach as a result of a phishing attack.
These are:
- Multi Factor Authentication
- Web filtering
- Email filtering
I’ll cover Multi Factor Authentication in a few moments as it helps to protect passwords generally, and not just from Phishing.
But web filtering and email filtering are two things that are often overlooked. You can filter your email and web traffic so that anything that looks suspicious is not allowed in before it even gets to your computer. Some of the software used to do this is really clever, using AI to determine if something doesn’t look right. If we can stop it in the first place then you are less likely to be taken in. Web filtering and email filtering often aren’t expensive either – often just a few pounds per month per user, so well worth the outlay.
Web and email filtering can also work on all devices, even when you are out and about, reducing the risk of picking up something nasty from a dodgy wifi network.
What about Social Engineering?
Perhaps less well known than Phishing is the wider problem of Social Engineering, of which Phishing is a subset.
If you have Facebook you will no doubt have seen this quizzes which pop up from time to time. In these two examples we have “What is Your Royal Guest name?” and “What would the movie title of your life be?” To find out the answer to these all important questions, all you have to do is answer some quite personal questions.

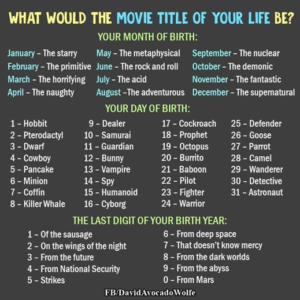
In the first example your surname is your pet’s first name.
That’s nice.
Your pet’s first name is a common password reset question or could even be your password itself.
So I could post that quiz on my Facebook page and very quickly get a list of people’s possible passwords, and quite possibly the password they use to get into Facebook.
Ever had your Facebook account hacked and wondered why? Maybe you did one of the quizzes and fell foul of Social Engineering.
The most recent one I saw challenged people to post pictures of their first car. This seems innocuous enough, until you realise that the make and model of your first car is an Office 365 password reset question.
If a scammer has your email address, which is quite possible as you might have listed it on your social media profile, or they might have hacked into a friend or colleague’s account – someone who frequently emails you – and also gets an answer to a password reset question, they don’t even need your password. They just login, select the reset password option and hey presto they are in your account – and you are locked out!
You might think this sounds a little far-fetched. But it isn’t. It happens.
So be careful what you share on Facebook or social media. Don’t be tempted to answer questions or quizzes that reveal information that could be used to compromise your security. Think first! It could save you some heartache and financial loss.
Stolen Credentials
In May 2019, Security Magazine reported that Canva, a graphic-design tool website, suffered a data breach that affected 139 million users. The data exposed included customer usernames, real names, email addresses, passwords and city and country information. In addition, of the total 139 million users, 78 million users had a Gmail address associated with their Canva account.
The hacker responsible for this breach has put up for sale on the dark web the data of 932 million users, which they stole from 44 companies from all over the world.
This kind of scenario is exactly why you need a different password for each account. Unfortunately, the websites we use on a day to day based are at risk of and do get hacked on a collective level. And a hacker knows that 80% of people re-se passwords. So breaking into Canva and getting usernames and password of Canva means they’ve probably got peoples usernames and passwords for other things too – facebook, gmail, instagram, whatever.
Plus these details are FOR SALE. So anyone can have a go!
This is not an isolated incident.
According to CSO Online the 15 biggest data breaches of the 21st century affected the following companies:
- Adobe
- Adult Friend Finder
- Canva
- Dubsmash
- eBay
- Equifax
- Heartland Payment Systems
- Marriott International
- My Fitness Pal
- MySpace
- NetEase
- Sina Weibo
- Yahoo
- Zynga
I guarantee you have an account with at least one of those.
There is a great website you can use to check if your email has ever been on one of these data breaches – https://haveibeenpwned.com. If your email is on there then obviously, you need to change your password on anything that uses the same password as the site that was hacked
Bottom line is, you can’t expect other people to look after your passwords – you need to do it yourself. A password manager is the way to go.
The Solution? – Multi Factor Authentication
Finally, there is one thing you can do to protect yourself from all of these risks.
The answer is not to rely on a password alone.
You can use something called Multi Factor Authentication (MFA), sometimes called Two-Factor Authentication or 2FA. This is the SECOND thing you need to do.
This dictates that you need something else in addition to your password to be able to login. It might be something you have, or something you know or something you are. It could be a fingerprint, or a passcode, or a mobile phone.
Essentially MFA means that even if your password is compromised, it is a useless piece of information, as it cannot be used to access your account without possession of the second factor.
You will be familiar with MFA as banks have been using for years. You will probably remember the dongles your bank would send you – maybe you still use one – that generated a code that you needed to enter in addition to your password. These days they send a notification to your phone app. Phones are a very common second factor in MFA as they are so ubiquitous.
More and more websites are now giving you the option to enable MFA. And if they offer it you should take it. This simple thing increases the security of your account almost infinitely.
And if websites don’t offer it, there are solutions for your business that can make it happen.
You’ll know this company
Google.
Google implemented MFA across its whole company in 2018 using security keys in addition to passwords. As a result they have not had a breach owing to phishing since.
And if it’s good enough for google, its good enough for us.
If you want put these security measures in place for your business then give us a call on 01482 298120 or use our contact form to get in touch.


